Filtering of traffic in monitor tab of paloalto helps us to find many things including
1.whether a traffic is getting allowed or denied
2.To filter traffic based on host, zone, port, action etc
3.To filter traffic between a specified time
4.Filter traffic from a particular user
5.Filter traffic to or from a specific IP /Network /Zone
In some cases we should have successfully created the policy in PaloAlto but we may forget to add the needed port in that rule.When a user is complaining that he is not able to access a particular service in a particular server we can easily figure out whats going on by reviewing the logs in monitoring tab of PaloAlto.
Login to PaloAlto and Goto Monitor > Traffic(left tab).There you can see the traffic flow .To change the automatic refresh interval, select an interval from the drop-down (1 min, 30 seconds, 10 seconds,or Manual).
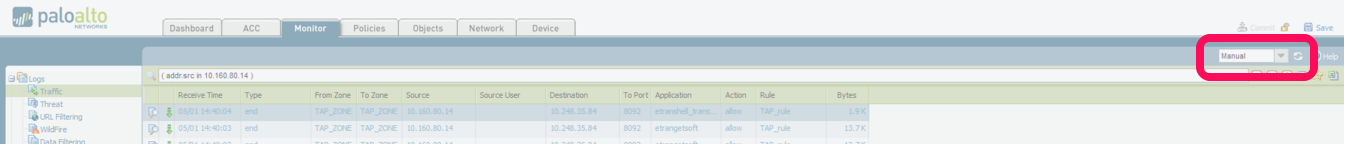
To change the number of log entries per page, select the number of rows from the Rows drop-down
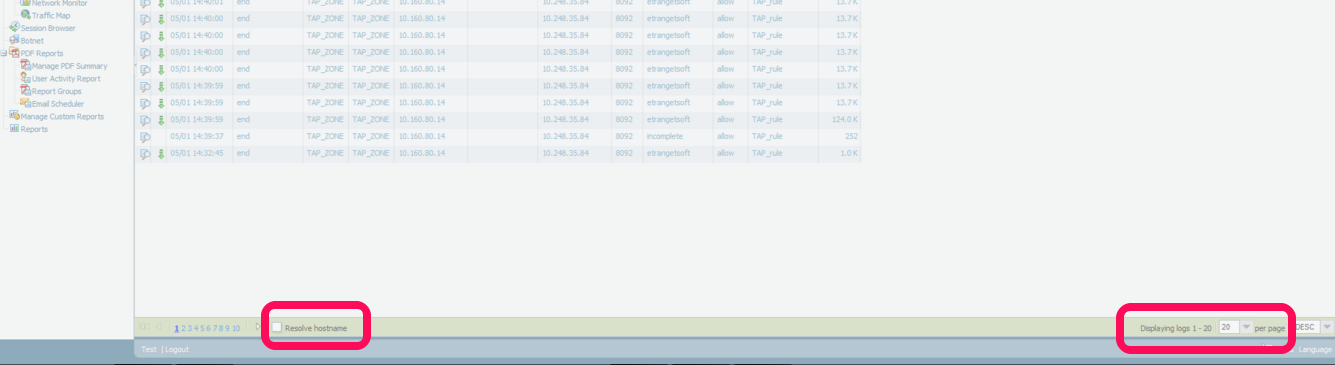
Select the Resolve Hostname check box to begin resolving external IP addresses to domain names.
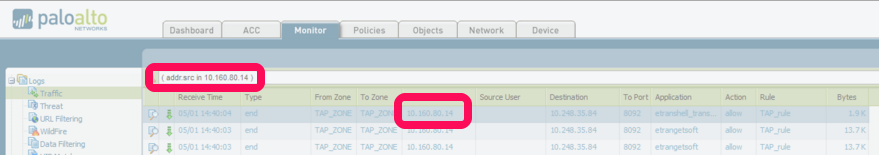
To filter traffic from source
1.Click on any IP in the source field2.It will automatically add addr.src in x.x.x.x in the filter bar. eg (addr.src in 10.160.80.14)
3.Press ENTER.
4.It will show all the traffic generating from 10.160.80.14
5.Edit IP as per your need.
Some other examples
Destination Filter: (addr.dst in 192.168.2.6) - shows all traffic with a destination address of a host that matches 192.168.2.6Filter a source network : ( addr.src in 192.168.10.0/24 ) - shows all traffic from network 192.168.10.0/24
Filter a destination network : (addr.dst in 192.168.10.0/24) - shows all traffic to network 192.168.10.0/24
Filter using Source and Destination
(addr.src in 1.1.1.1) AND (addr.dst in 2.2.2.2) - shows all traffic coming from a host with an IP address of 1.1.1.1 and going to a host destination address of 2.2.2.2Filter for source OR destination
(addr in 1.1.1.1) - Shows all traffic with a source OR destination address of a host that matches 1.1.1.1Zone Traffic Filter Examples
FROM ZONE TRUST
(zone.src eq TRUST) - shows all traffic coming from the TRUST zoneTO ZONE UNTRUST
(zone.dst eq UNTRUST) - shows all traffic going out the UNTRUST zone(zone.src eq TRUST) and (zone.dst eq UNTRUST) - shows all traffic traveling from the TRUST zone and going out the through UNTRUST
PORT Traffic Filter Examples
FROM PORT 22
(port.src eq 22)- shows all traffic traveling from source port 22TO PORT 80
(port.dst eq 80)- shows all traffic traveling to destination port 80Allowed/Denied Traffic Filter Examples
ALL TRAFFIC THAT HAS BEEN ALLOWED BY THE FIREWALL RULES
(action eq allow)OR
(action neq deny)
Example: (action eq allow)- Shows all traffic allowed by the firewall rules.
NOTE: Placing the letter 'n' in front of 'eq' means 'not equal to,' so anything not equal to 'deny' is displayed, which is any allowed traffic.
ALL TRAFFIC DENIED BY THE FIREWALL RULES
(action eq deny)OR
(action neq allow)
Example: (action eq deny) - Shows all traffic denied by the firewall rules.
NOTE: Placing the letter 'n' in front of 'eq' means 'not equal to,' so anything not equal to 'allow' is displayed, which is any denied traffic.
TRAFFIC from a particular user
(user.src eq 'Sysnet\Shabeer') - Shows traffic from that particular user [Sysnet is domain and shabeer is username]Combining Traffic Filter Examples
Show denied traffic from SOURCE 123.24.10.23
(addr.src in 123.24.10.23 ) and (action eq deny)Allowed TRAFFIC FROM SOURCE 11.10.21.21 to DESTINATION ADDRESS 20.20.20.56 in PORT 80
(addr.src in 11.10.21.21) and (addr.dst in 20.20.20.56) and (port.dst eq 80) and (action eq allow)ALL TRAFFIC FROM ZONE DEVELOPMENT AND SOURCE NETWORK 11.10.21.0/24 TO DESTINATION ADDRESS 20.20.20.21 IN THE SECURITY ZONE:
(zone.src eq DEVELOPMENT) and (addr.src in 11.10.21.0/24) and (addr.dst in 20.20.20.21) and (zone.dst eq SECURITY)NOTE : You don't need to remember any of the filters mentioned above.Its very simple to create even complex filters .You can simply click the needed criteria on the logs and it will automatically add to the filtering.You just need to edit the particular zone/IP address/Port number or Action
For example
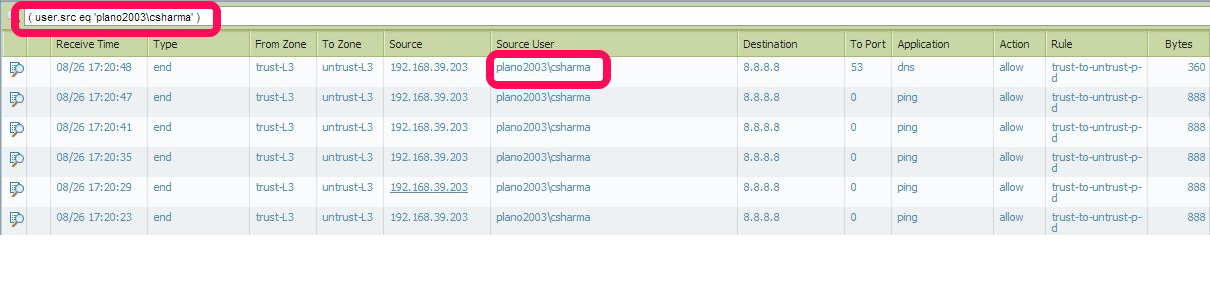
Below screenshot shows traffic from user plano2003\csharma. If you want to search custom user all you need to do is to
1. Click on any user below "Source user" here it is (user.src eq 'plano2003\csharma')
2.Then it will add(user.src eq 'plano2003\csharma') to the filter bar. edit it with your custom username
 Conclusion
Conclusion
1.To create a filter go to Monitor > Traffic
2. Just CLICK on the custom field you need to make a filter ie click on any field under From Zone / To Zone / Source / Source user / Destination / To port / Application / Action .In the above example we create filter using source user
3.Edit the IP/ZONE/PORT/ACTION as per your need
4..Press ENTER and it will show the custom traffic you need to see.
4..Press ENTER and it will show the custom traffic you need to see.
0 comments:
Post a Comment